Navigating the Digital Battlefield: A Comprehensive Look at Cyber Attack Maps
Related Articles: Navigating the Digital Battlefield: A Comprehensive Look at Cyber Attack Maps
Introduction
In this auspicious occasion, we are delighted to delve into the intriguing topic related to Navigating the Digital Battlefield: A Comprehensive Look at Cyber Attack Maps. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Navigating the Digital Battlefield: A Comprehensive Look at Cyber Attack Maps

The digital landscape is a dynamic and ever-evolving environment, constantly under threat from malicious actors. These threats manifest in various forms, ranging from simple phishing scams to sophisticated nation-state-sponsored attacks. Understanding the nature and location of these cyberattacks is crucial for bolstering cybersecurity defenses and mitigating potential damage. This is where cyber attack maps emerge as invaluable tools, providing real-time insights into the global cyber threat landscape.
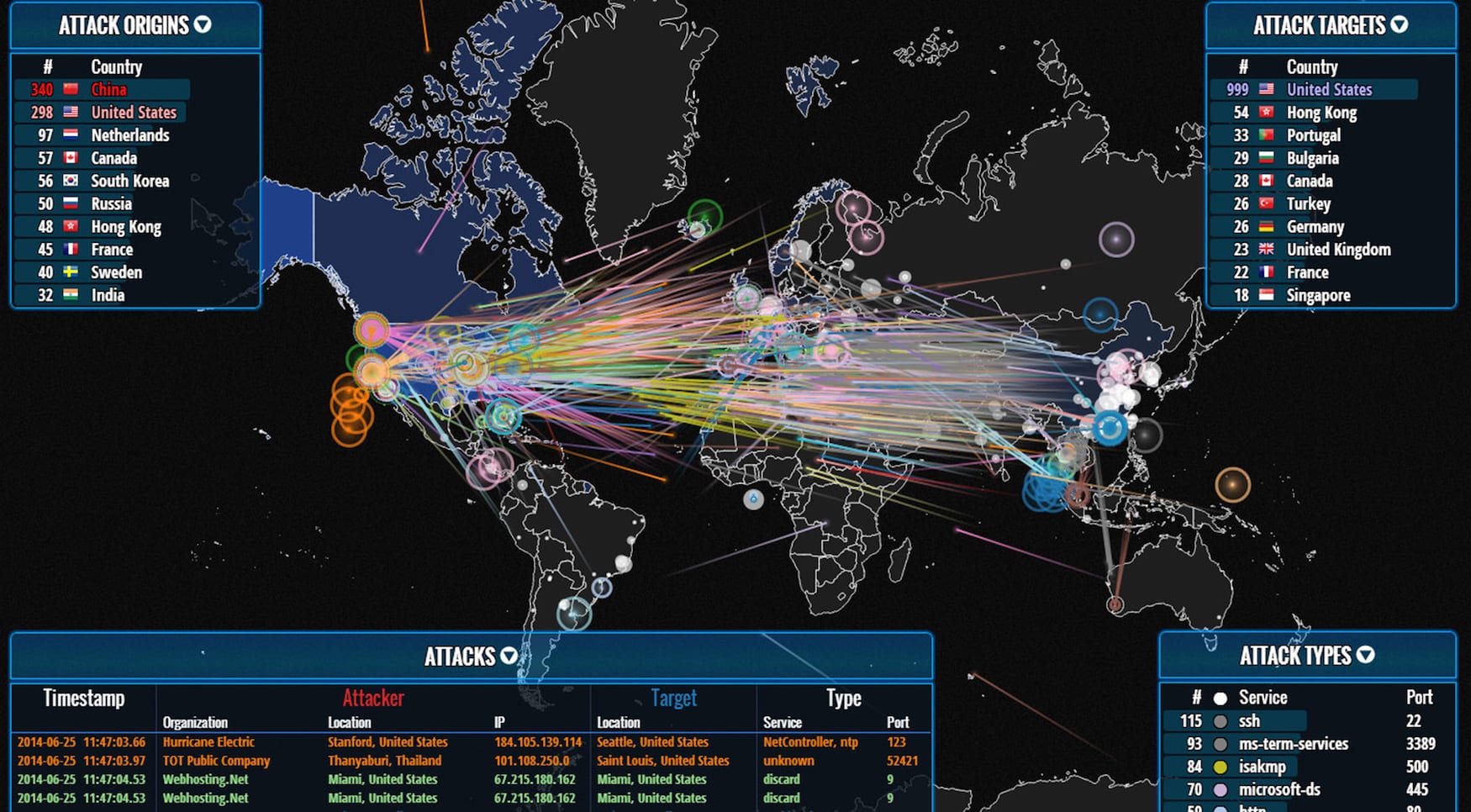
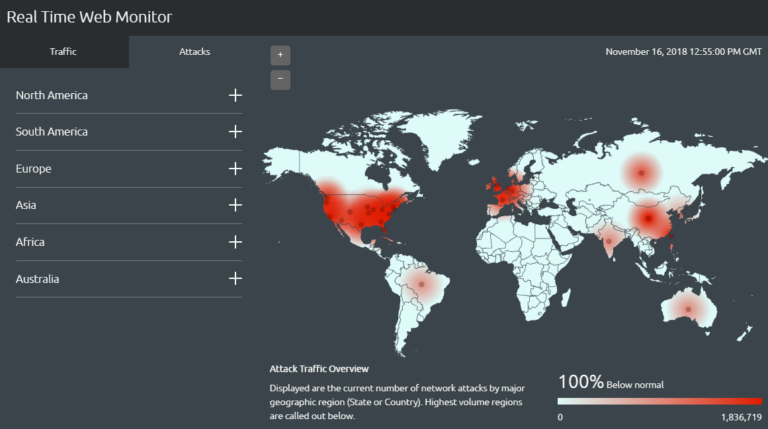
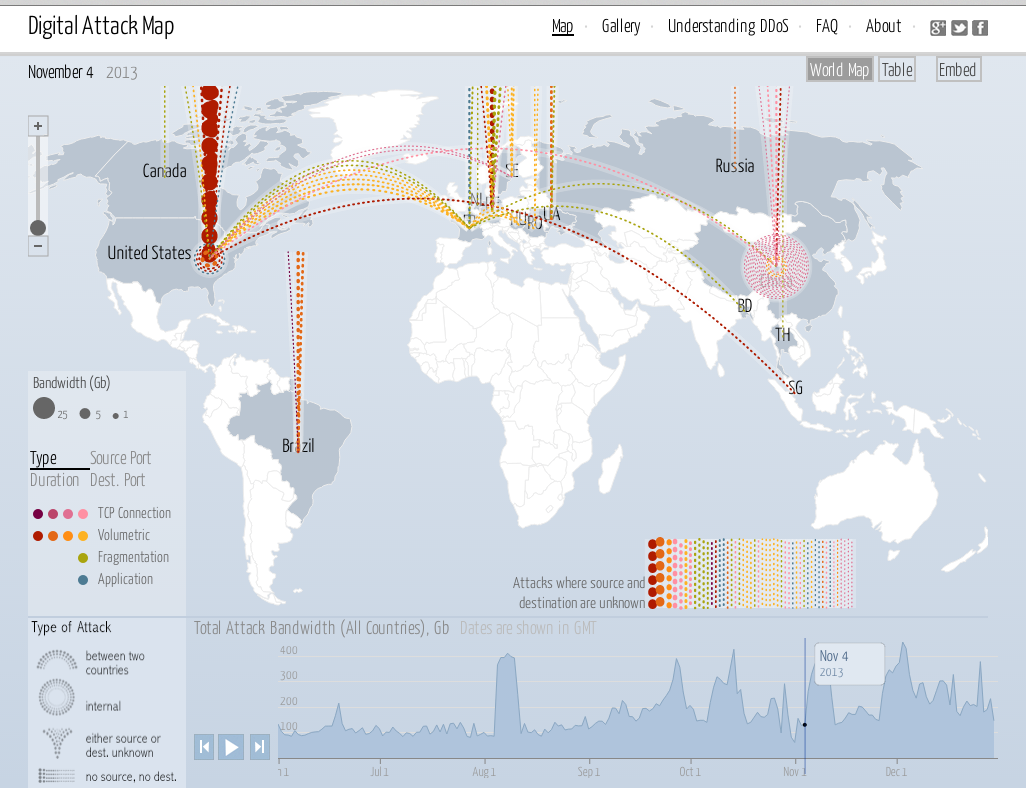
Cyber Attack Maps: A Visual Representation of Digital Warfare
Cyber attack maps are interactive visualizations that depict the global distribution and intensity of cyberattacks. They serve as a central hub for collecting and presenting data on various cyber threats, including:
- Geographic location: Identifying the origin and target locations of attacks, highlighting regions with heightened activity.
- Attack type: Categorizing attacks based on their methods, such as malware distribution, phishing campaigns, or denial-of-service attacks.
- Targets: Identifying the sectors or organizations most frequently targeted, be it government institutions, financial institutions, or critical infrastructure.
- Attack frequency: Tracking the temporal trends in cyberattacks, revealing periods of heightened activity or specific attack patterns.
The Benefits of Utilizing Cyber Attack Maps
Cyber attack maps offer a multitude of benefits for various stakeholders:
- Enhanced situational awareness: By providing a real-time overview of the cyber threat landscape, maps allow organizations and individuals to stay informed about potential threats and proactively adjust their security measures.
- Improved threat intelligence: Maps can be used to identify emerging threats, analyze attacker tactics, and gain insights into the motivations behind attacks. This information is vital for developing effective countermeasures and improving security protocols.
- Strategic decision-making: By understanding the geographic distribution and temporal patterns of cyberattacks, organizations can prioritize their security investments and allocate resources effectively.
- Risk assessment and mitigation: Maps enable organizations to assess their vulnerability to specific types of attacks and implement appropriate security measures to mitigate potential risks.
- Public awareness and education: These maps serve as valuable educational tools, raising public awareness about the nature and extent of cyber threats, encouraging individuals and organizations to adopt best practices for cybersecurity.
Types of Cyber Attack Maps
Cyber attack maps come in various forms, each offering unique perspectives and data points:
- Global maps: These maps provide a broad overview of cyberattacks worldwide, highlighting regions with high attack frequency and specific attack types.
- Sector-specific maps: These maps focus on specific industries or sectors, such as finance, healthcare, or energy, providing insights into the threats faced by these industries.
- Attack-type specific maps: These maps concentrate on specific attack types, such as malware distribution, phishing campaigns, or ransomware attacks, offering detailed information about the techniques and tactics employed.
- Temporal maps: These maps track the evolution of cyberattacks over time, revealing trends and patterns in attack frequency and intensity.
FAQs about Cyber Attack Maps
1. What are the limitations of cyber attack maps?
While cyber attack maps provide valuable insights, they are not without limitations. The accuracy and completeness of the data depend on the reporting mechanisms and the willingness of organizations to share information. Additionally, maps may not capture all cyberattacks, particularly those that go undetected or are not reported.
2. How can I access cyber attack maps?
Various organizations and research institutions provide publicly accessible cyber attack maps. Some examples include:
- Cybersecurity and Infrastructure Security Agency (CISA): Offers resources and information on cyber threats and vulnerabilities.
- National Institute of Standards and Technology (NIST): Provides guidance and best practices for cybersecurity.
- FireEye: A cybersecurity company that offers threat intelligence and analysis services.
- Recorded Future: A threat intelligence platform that provides real-time insights into cyber threats.
3. How can I use cyber attack maps to improve my cybersecurity?
- Identify potential threats: Analyze the attack types and targets highlighted on the maps to assess your organization’s vulnerability.
- Develop targeted security measures: Implement security controls specifically designed to mitigate the risks identified on the maps.
- Stay informed about emerging threats: Monitor the maps regularly to stay updated on new attack trends and tactics.
- Share information with your team: Educate your employees about the threats highlighted on the maps and encourage them to report suspicious activity.
Tips for Utilizing Cyber Attack Maps Effectively
- Choose reputable sources: Ensure the maps you use are from reliable and trusted sources, such as government agencies or reputable cybersecurity companies.
- Understand the data: Familiarize yourself with the data presented on the maps, including the methodology used to collect and analyze the information.
- Interpret the data: Analyze the trends and patterns revealed by the maps and use this information to inform your security decisions.
- Combine with other intelligence: Integrate the information from cyber attack maps with other threat intelligence sources to gain a comprehensive understanding of the cyber threat landscape.
Conclusion
Cyber attack maps are essential tools for navigating the complex and ever-evolving world of cybersecurity. By providing real-time insights into the global distribution and intensity of cyberattacks, these maps enable organizations and individuals to make informed decisions about their security posture, mitigate potential risks, and stay ahead of emerging threats. As the digital landscape continues to evolve, the role of cyber attack maps in safeguarding our online world will only grow more critical.





Closure
Thus, we hope this article has provided valuable insights into Navigating the Digital Battlefield: A Comprehensive Look at Cyber Attack Maps. We hope you find this article informative and beneficial. See you in our next article!